There are four items that control network bandwidth utilization within SCCM:
- BITS client setting – The download of data
from the distribution point to the client is a BITS download. In the
client settings of the clients the rate of those downloads can be
adjusted. However, this is client side and does not know about
bandwidth on the network so if enough clients, even if all configured to
1Mbps, are trying to download at the same time it can still clog the WAN.
https://learn.microsoft.com/en-us/mem/configmgr/core/clients/deploy/about-client-settings#background-intelligent-transfer-service-bits
I recommend setting the BITS settings but to something that will work for your organization. Exactly what that is varies greatly from one organization to another. - Rate Limit Schedules – Set in the Distribution Point properties, this controls
maximum data that can be sent to each distribution point at any given time of
day. This is to prevent WAN saturation while getting the data onto the distribution points prior to deployment to clients.
https://learn.microsoft.com/en-us/mem/configmgr/core/plan-design/hierarchy/manage-network-bandwidth#BKMK_PlanningForThrottling
I recommend setting the rate limits but to something that will work for your organization. Exactly what that is varies greatly from one organization to another. Remember that this is set individually for each distribution point.
- LEDBAT - Where BITS worked client side, LEDBAT works server side to control bandwidth usage. Like the throttling rate limits it
is enabled on each distribution point individually. The idea is that it dynamically adjusts
transfer rates so that clients only use network bandwidth when it's
available.
https://learn.microsoft.com/en-us/mem/configmgr/core/plan-design/hierarchy/fundamental-concepts-for-content-management#windows-ledbat
I recommend turning this on for every distribution point.
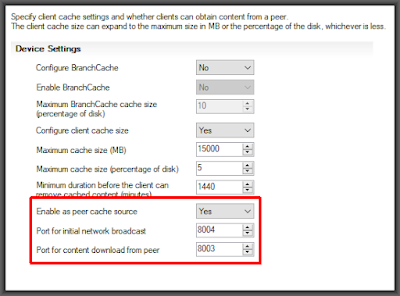
- Peer caching
technologies
– Peer caching takes at least a portion of the load off of the WAN by
allowing clients to share cached deployment data with each other. We
would limit this to only peers that are on the same subnet in order to
ensure that they are never going cross-WAN. There are three peer caching
technologies available in SCCM. Without going deep on all of them I
will just say that the on I recommend using is “Peer cache” for on-premises and Delivery Optimization for cloud (Intune). Yes, use both if you have both on-prem SCCM and Intune because Delivery Optimization gives no benefit to your Line-of-Business applications or anything else that is not delivered from Microsoft's global distribution network.
https://learn.microsoft.com/en-us/mem/configmgr/core/plan-design/hierarchy/fundamental-concepts-for-content-management#peer-caching-technologies
I suggest turning on Peer Cache for all non-VPN connected clients and enabling peer downloads, but limited to same subnet, on all non-VPN boundary groups.